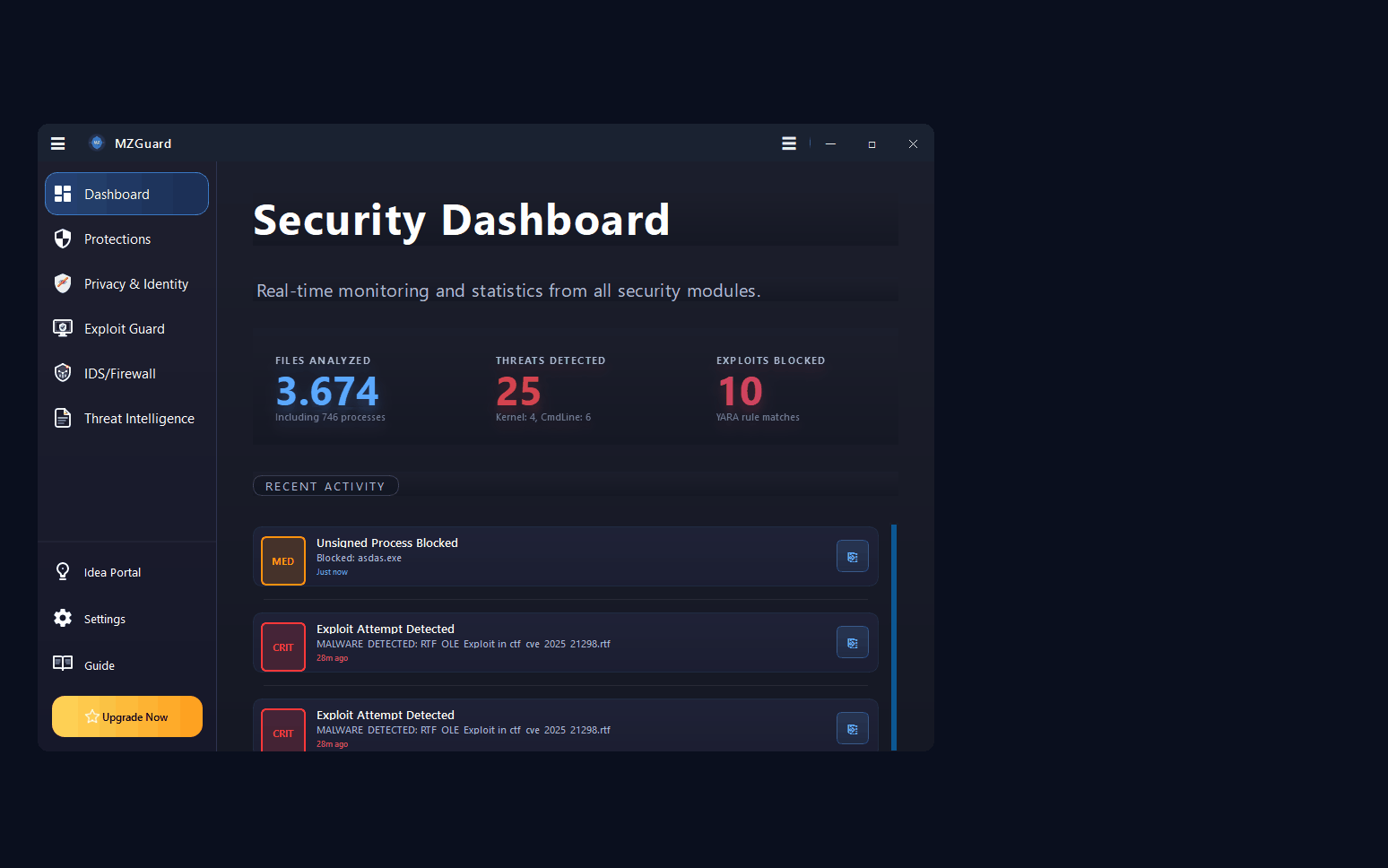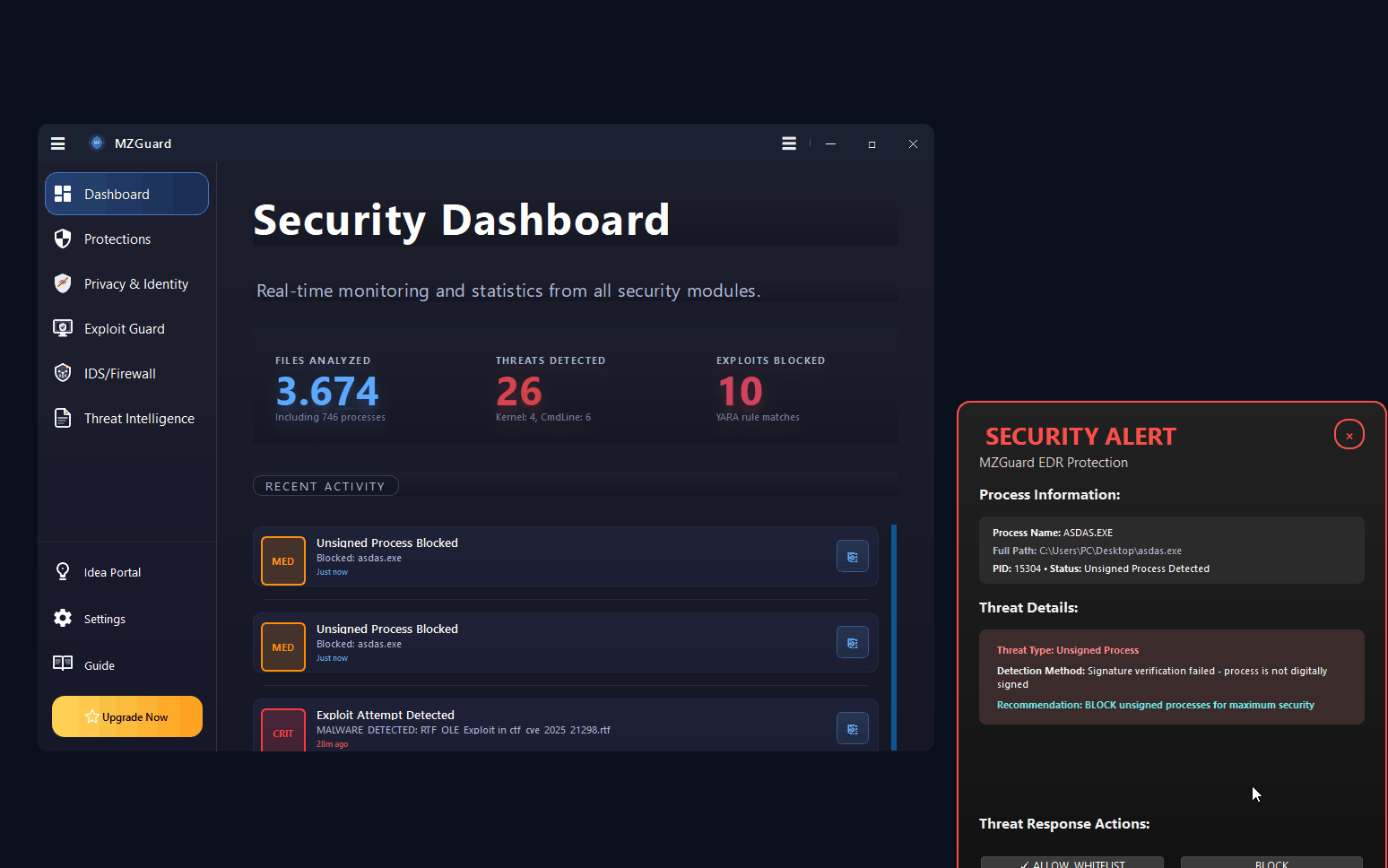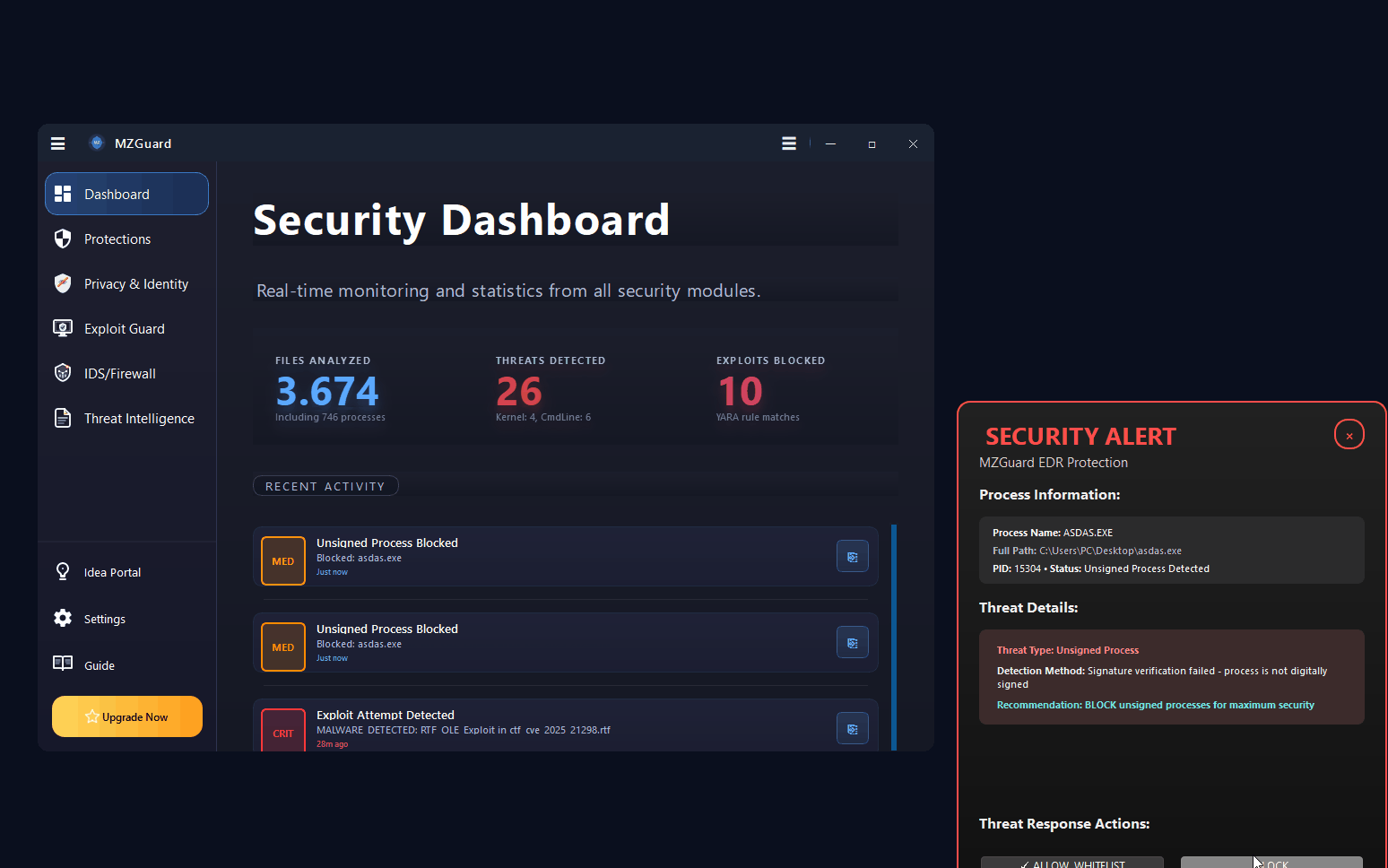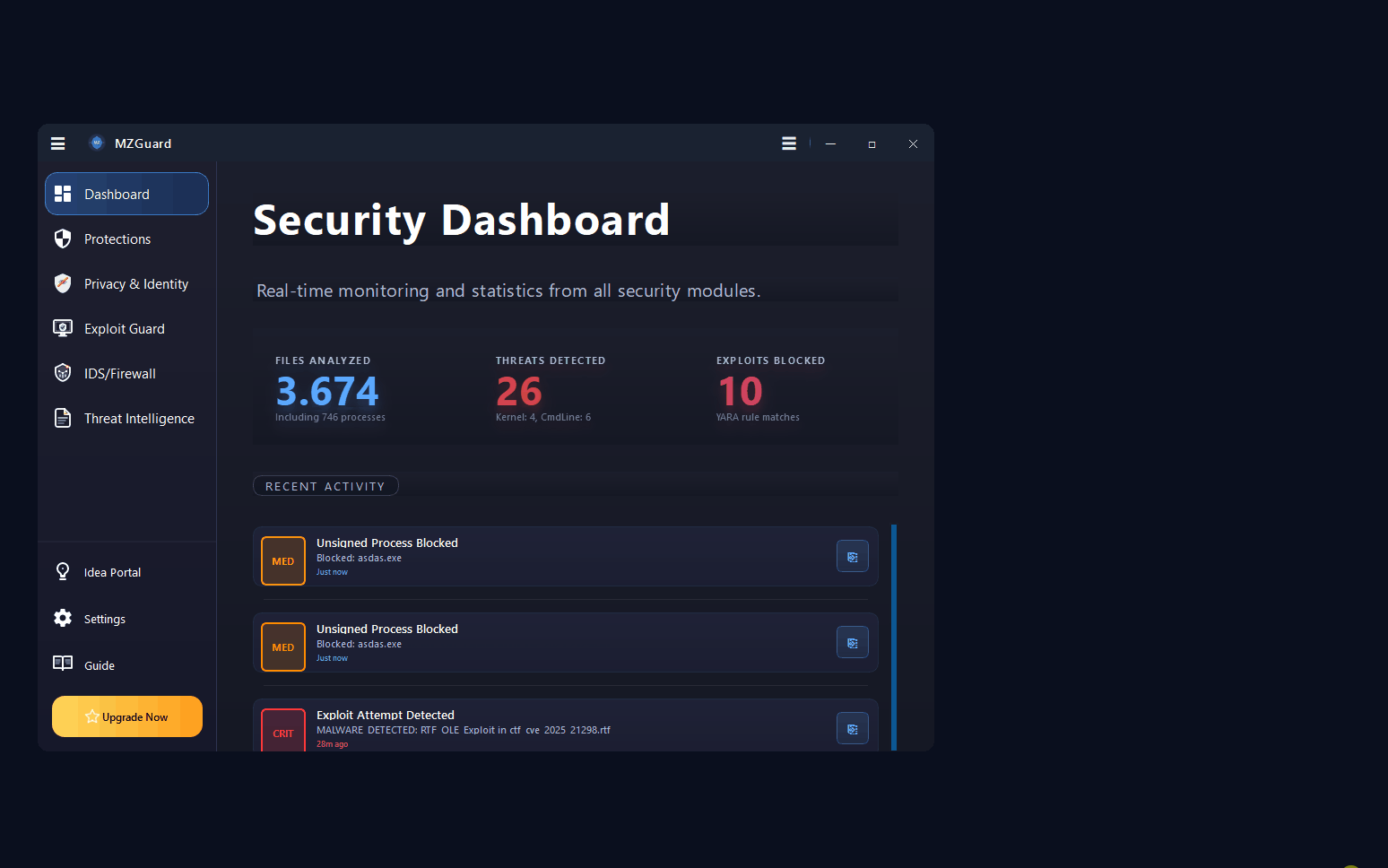
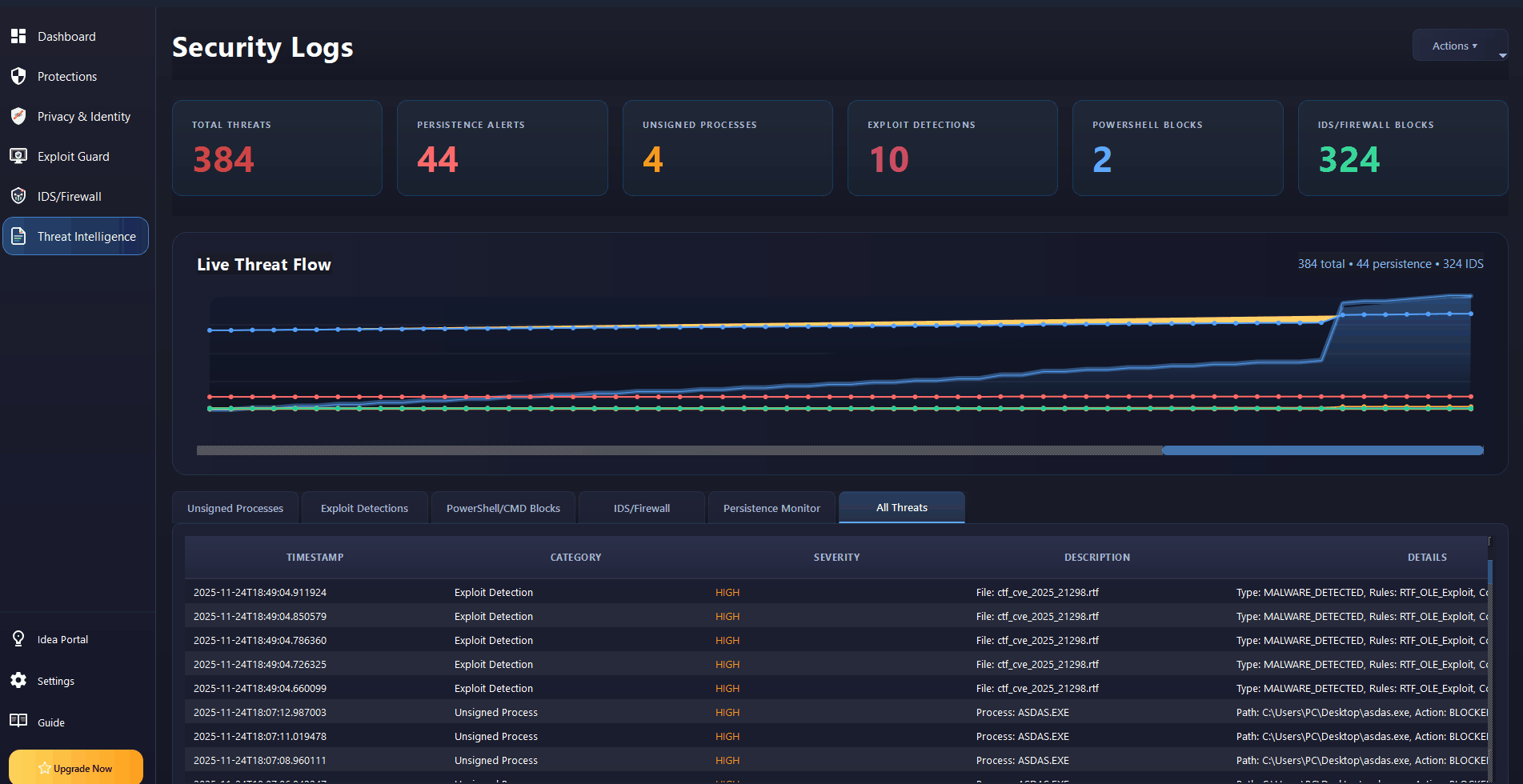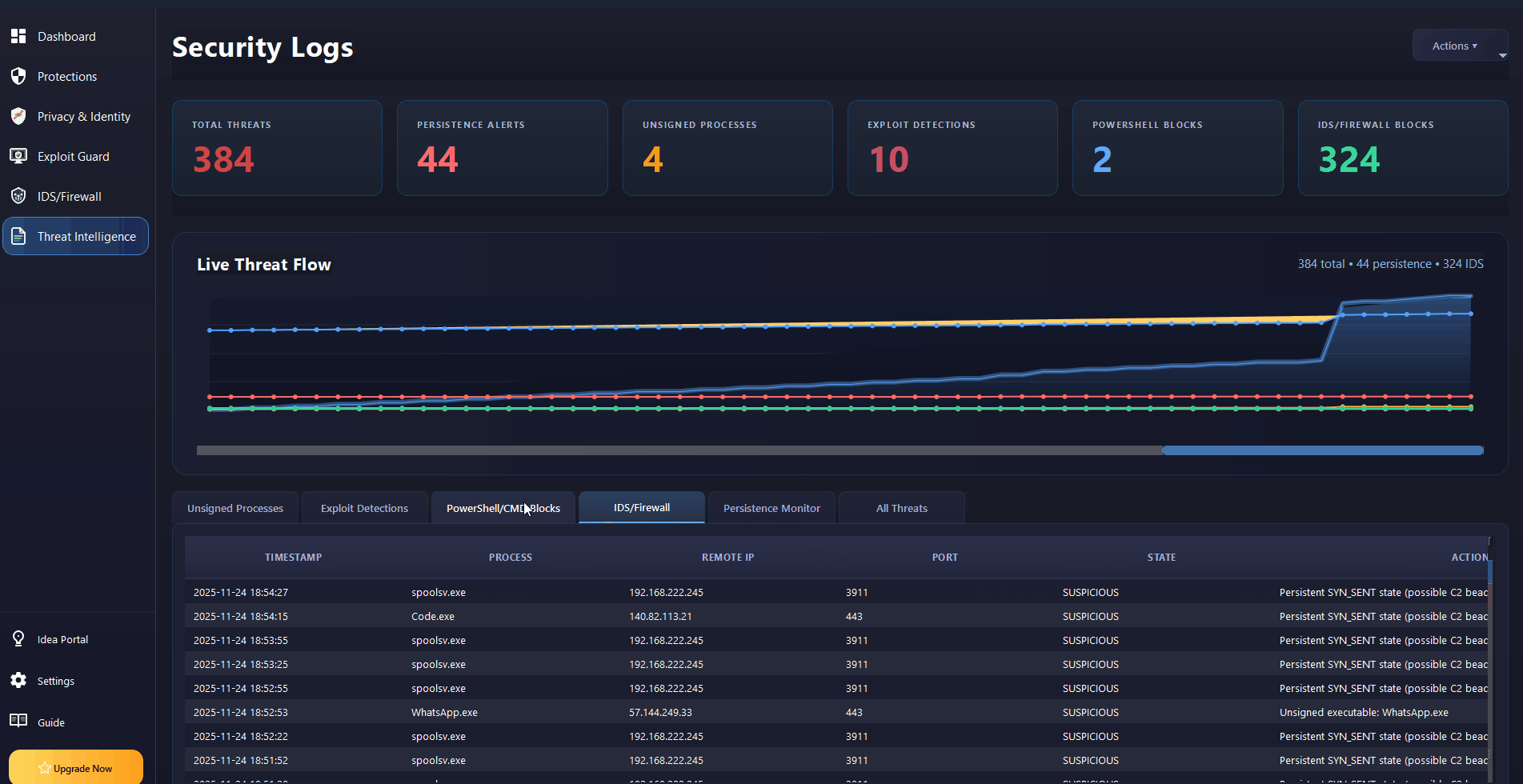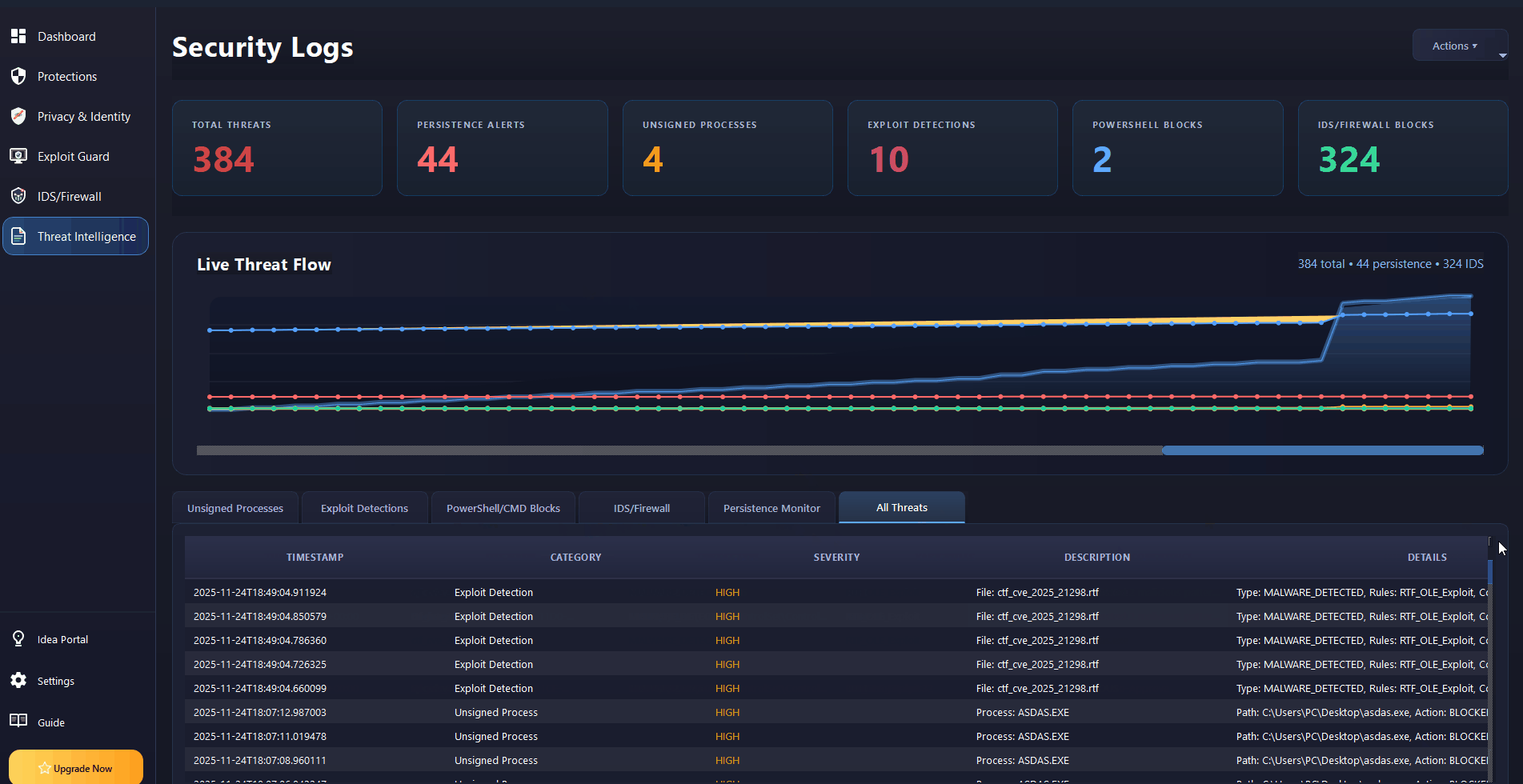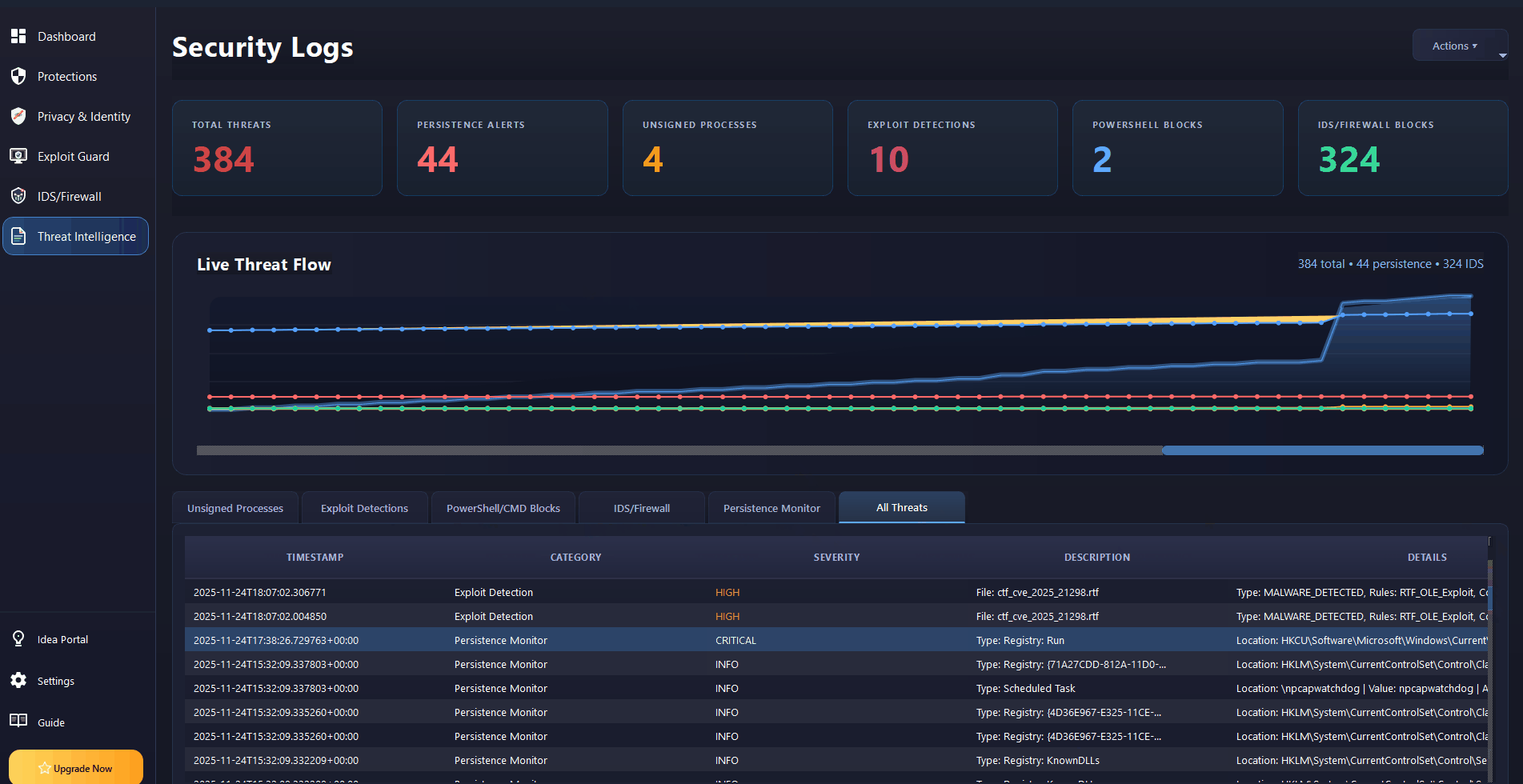
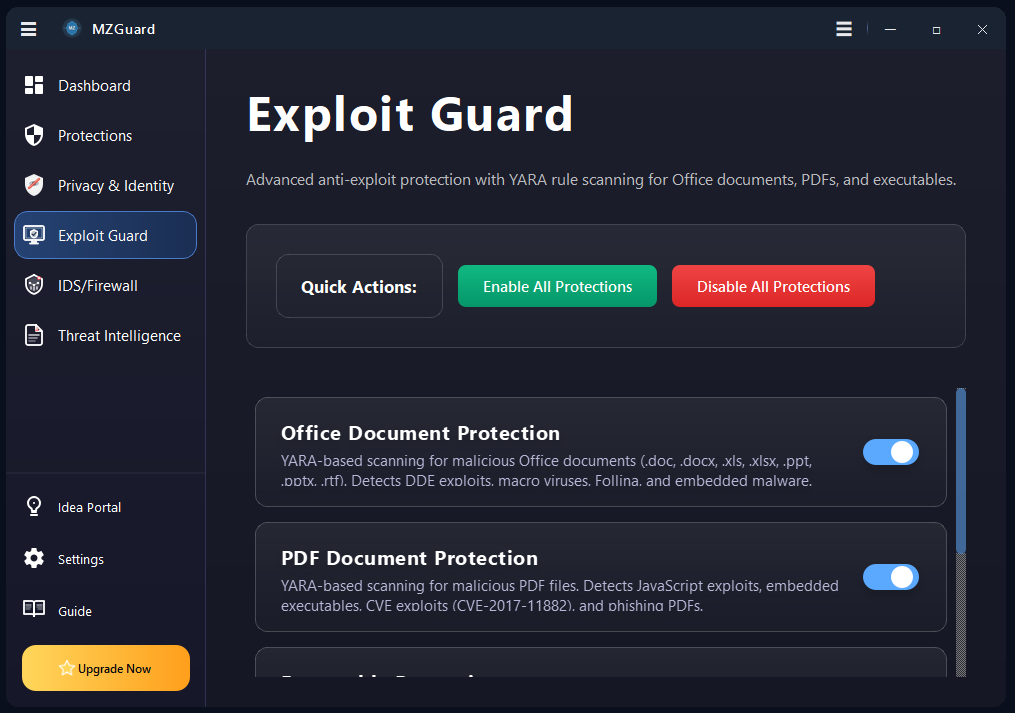
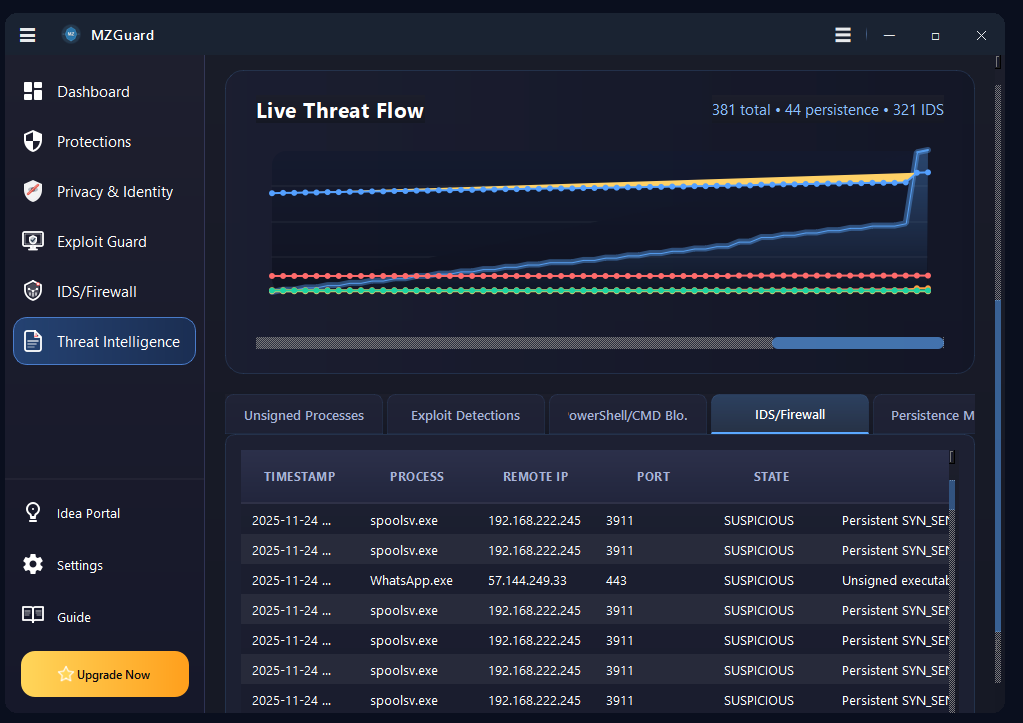
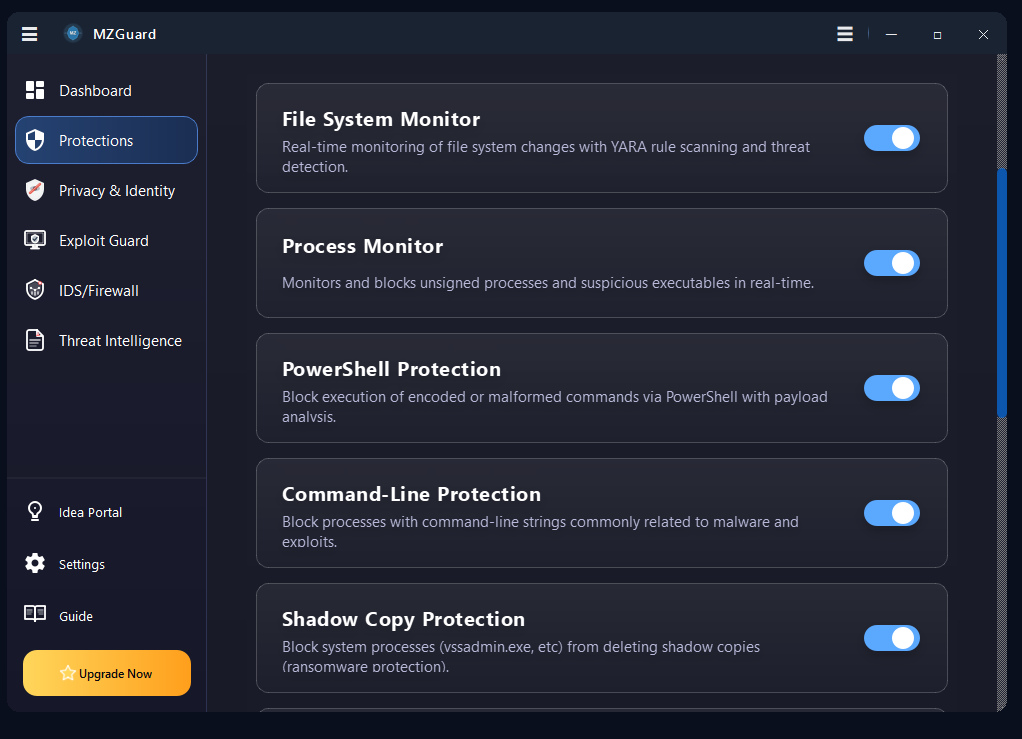
MZGuard Endpoint Security: Real-time Ransomware & Malware Defense for Windows.
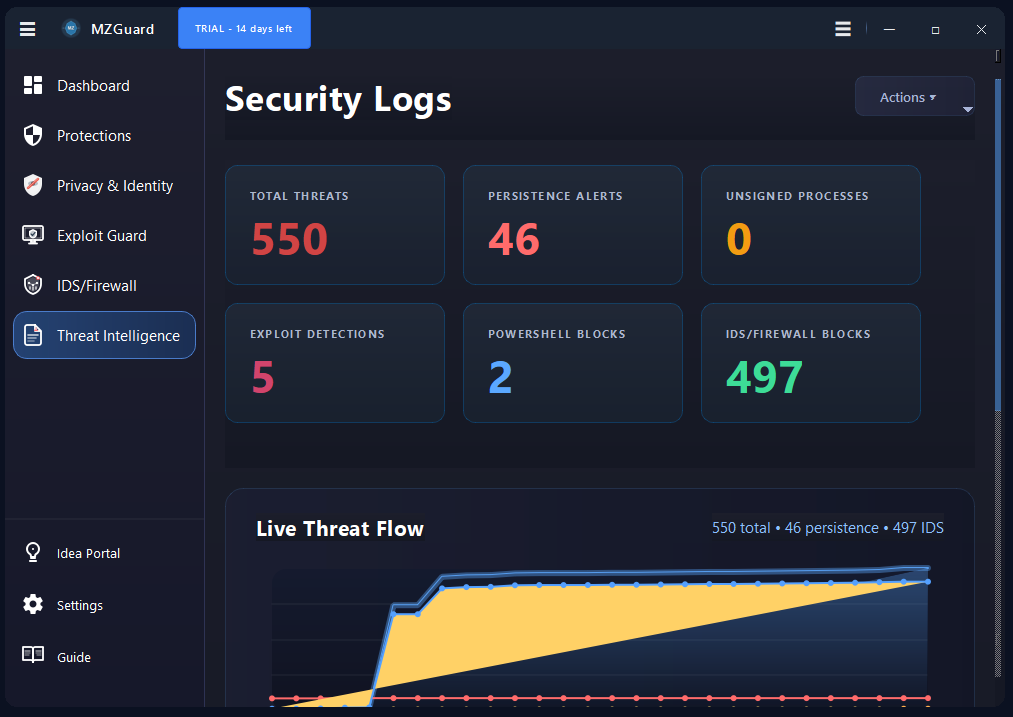
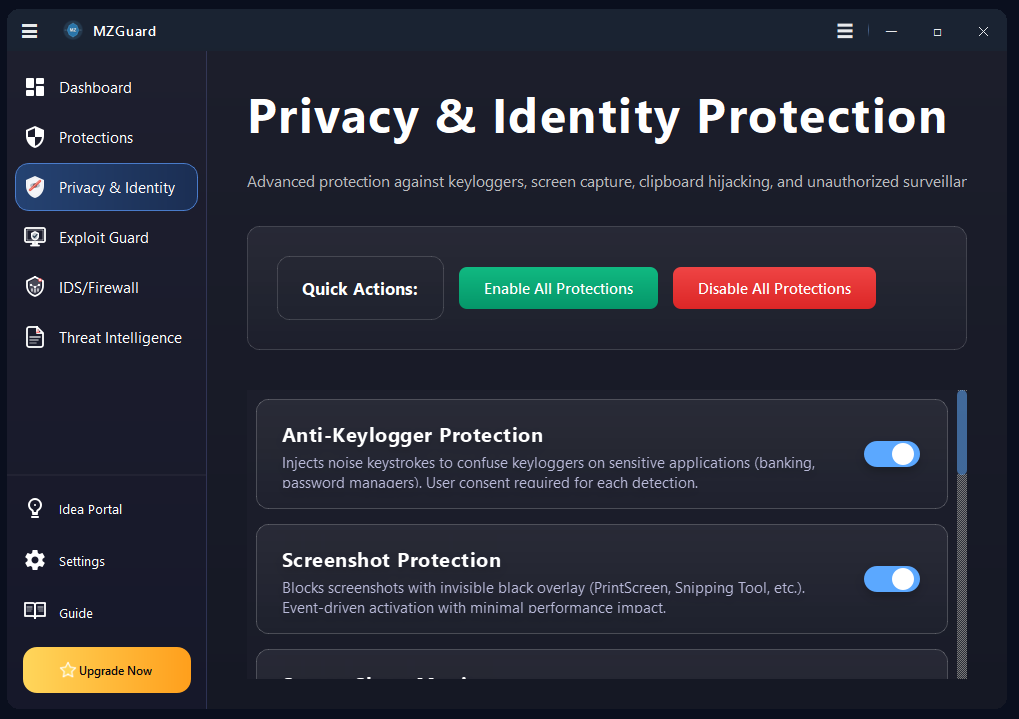
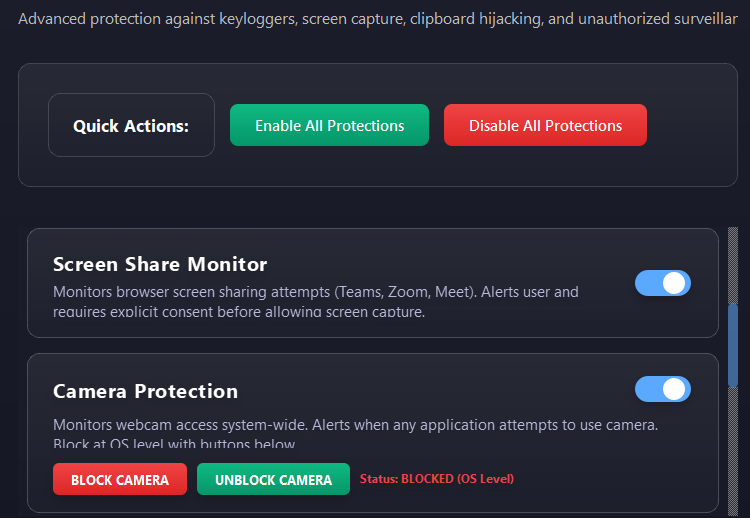
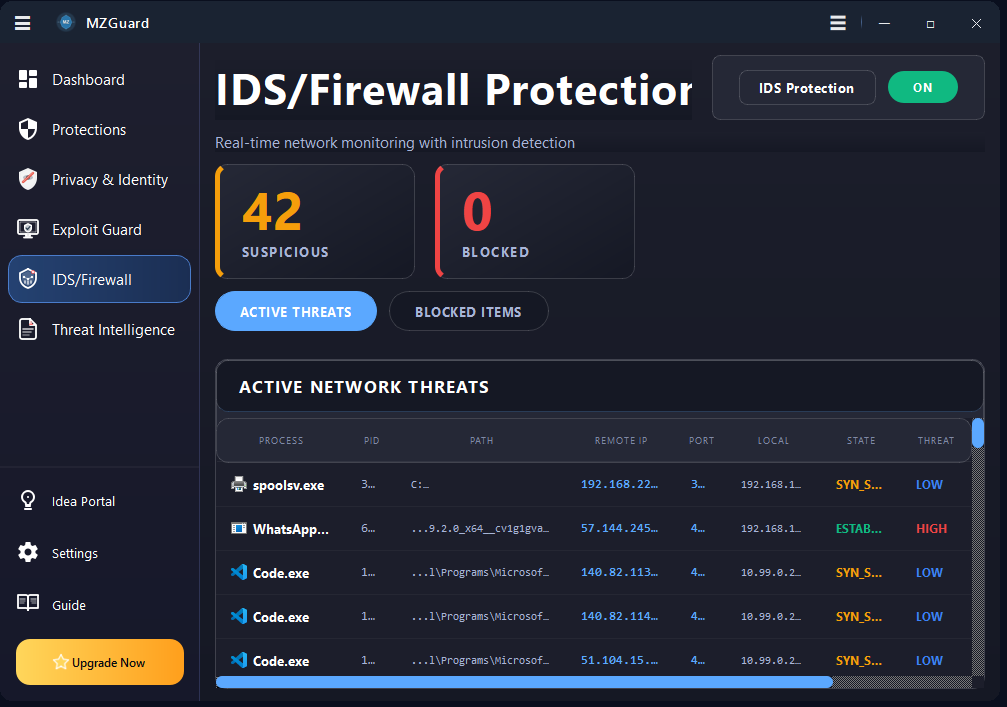
Endpoint security and malware defense for Windows 7, 10, 11 & Server. Real-time ransomware protection, anti-keylogger shields, PowerShell controls, and IDS/Firewall monitoring. Works alongside your existing antivirus.